Capture the Flag Learning Path (Special Offer)
Strengthen Your Pentesting Skills Through Capture the Flag Exercises
Build your own virtual lab environment. Learn to use pentesting tools to enumerate and gain root access, and the different attack vectors used to exploit a target.
Original Price: $149
Limited-Time Offer: $79

Mastering Digital Forensics Learning Path (Special Offer)
Mastering Digital Forensics
Learn to detect and backtrack cyber criminals and hackers with digital forensics!
Original Price: $199
Limited-Time Offer: $79

Bug Bounty Hunting Essentials Learning Path (Special Offer)
Bug Bounty Hunting Essentials
Learn to hunt high-impact vulnerabilities through hands-on examples and real-world tricks!
Original Price: $149
Limited-Time Offer: $79

Cybersecurity Fundamentals for Beginners (Special Offer)
Learn Everything You Need to Become a Secure Cyber Professional with a Hands-on Learning Path!
Get Immediate Access to 173 Premium Lessons with This Incredible Offer
Original Price: $199
Limited-Time Offer: $79

The Ultimate JavaScript Bundle (Special Offer)
The Ultimate JavaScript Bundle
Master JavaScript with Hands-on Exercises and Real-World Projects!
Original Price: $199
Limited-Time Offer: $79

Practical Artificial Intelligence for Professionals (Special Offer)
Learn How to Use Artificial Intelligence to Achieve Automation, Predictions, Analysis and Better Decision Making!
Get Immediate Access to 269 Premium Lessons with This Incredible Offer
Original Price: $199
Limited-Time Offer: $79

Mastering Open Source Intelligence Learning Path (Special Offer)
Master Open-Source Intelligence
Three premium courses that train you in gathering intelligence from published sources to support your intelligence needs
Original Price: $149
Limited-Time Offer: $79
More specialized on-demand courses
Access Control
Topics Covered Access Control Models Permissions, Rights, Privileges Implicit...
Application Security
Topics Covered Cloud-Secure Software Development Lifecycle (SDLC) ISO ISO/IEC...
Architecture and Design
Program Objectives Explain the importance of security concepts in...
Assessments and Audits
Topics Covered Audit Frameworks Assessments and Audits Security Audit...
Attacks and Exploits
Program Objectives Research attack vectors and perform network attacks...
Automation and Scripting
Program Objectives Given a scenario, deploy and execute basic...
Bash Programming
Topics Covered What is Bash Programming? What is a...
Biometrics
Topics Covered Fingerprint Iris – iris recognition Facial Voice...
Blockchain
Topics Covered What is Blockchain? The history of Bitcoin...
Blue Team – Case Study
Topics Covered Intro to case study What is live...
Blue Team Methodology
Topics Covered 1. Intro what is the blue team...
ChatGPT (Impacts of Chatbots and ChatGPT)
Topics Covered What is ChatGPT ChatGPT Achievements so far...
Cloud Architecture and Design
Program Objectives Compare and contrast the different types of...
Cloud Cybersecurity
Topics Covered Why Cybersecurity CIA Triad NIST Cloud Computing...
Cloud Deployment
Program Objectives Given a scenario, integrate components into a...
Cloud operations and support
Program Objectives Given a scenario, configure logging, monitoring, and...
Cloud Penetration Testing
Topics Covered What Is Cloud Pen Testing What is...
Cloud Security
Program Objectives Given a scenario, configure identity and access...
Cloud Security – Cyber Security
Topics Covered Cloud Model Cloud organization Cloud Components
Communication & Change Management
Project Objectives Given a scenario, use the appropriate communication...
Compliance
Topics Covered Security Governance Regulatory Compliance Compliance Strategic Plan...
Compliance and Assessment
Program Objectives Understand the importance of data privacy and...
Cryptography and PKI
Topics Covered What Is cryptography? Cryptography Techniques Types of...
Cybersecurity fundamentals – Network Essentials
Topics Covered is the Internet of Things? How loT...
Data Protection
Topics Covered Data in Transit Data in Use Data...
Enterprise Security Architecture
Program Objectives Analyze a scenario and integrate network...
Enterprise Security Operations
Program Objectives Given a scenario, conduct a security...
Exploit Frameworks/Exploit Kits
Topics Covered Intro to Exploits Zero Day Exploit Vulnerabilities...
Exploiting OS
Topics Covered Understanding Control Types Metasploit Pwning Windows with...
Fedramp Best Practices
Topics Covered FedRAMP process/flowchart Preparation/Authorization/Continuous Monitoring Selecting a FedRAMP...
Fedramp Continuous Monitoring Strategy
Topics Covered Roles and Responsibilities within the ConMon Process...
Fedramp Security Assessment Plan
Topics Covered What is a Security Assessment Plan? Laws,...
Fedramp System Security Plan (SSP) Control
Topics Covered What documents are required for initial package...
Git and Github
Topics Covered What is Github? Why is Github important...
Governance, Risk, and Compliance
Program Objectives Compare and contrast various types of controls....
Hardware and System Configuration
Program Objectives Explain Linux boot process concepts. Given...
Identity and Access (IAM)
Topics Covered 1. What is identity and access management?...
IDM (PAM, IAM)
Topics Covered Controlling Access to Assets Comparing Identification and...
Implementation
Program Objectives Given a scenario, implement secure protocols Given...
Incident Response
Program Objectives Explain the importance of the incident response...
Incident Response Toolkit
Topics Covered Incident Response Toolkit How IR Management Tools...
Information Gathering and Vulnerability Scanning
Program Objectives Perform passive reconnaissance Perform active reconnaissance Analyze...
Infrastructure as a Service
Topics Covered What is the laaS laas Delivery laaS...
Internet of Things
Topics Covered What is the Internet of Things? How...
Introduction to Pentesting
A penetration test, colloquially known as a pen test...
Kali Linux
Topics Covered What is Linux? Windows V/s Linux OS...
Kali Linux Bash Scripting
Topics Covered What is Bash Programming? What is a...
Kali Linux Command Line Fundamentals
Kali Linux Commands is an advanced penetration testing distribution...
Kali Services
Topics Coved Configuring Network Managing User & Groups Configuring...
LAMP stack
Topics Covered Web server What is a LAMP stack?...
Legal/Regulatory Compliance
Topics Covered Identify Legal Requirements pertaining to Red Team...
Linux Firewalls
Topics Covered What Is Firewall How Firewalls Work Types...
Linux Package Management
Topics Covered Introduction to apt & dpkg Kali Repositories...
Linux Troubleshooting and Diagnostics
Program Objectives Given a scenario, analyze system processes in...
Mobile Device Hacking
Topic Covered Introduction to Mobile Device Hacking OWASP Top...
Monitoring and Managing Linux Processes
Topics Covered Security Policy Security Measures Securing Network Services...
Network Design
Topics Covered Packet Capture and Replay Packet Sniffer Protocol...
Operations and Incident Response
Program Objectives Given a scenario, use the appropriate tool...
OSINT and Information Gathering
Topics Covered What is Information Gathering? What Information is...
Package Management and Repositories
Topics Covered Introduction to apt & dpkg Kali Repositories...
Password Cracking
Topics Covered Password Attack types Attack tools Attack demo...
Physical Security Penetration Testing
Topics Covered Physical Security Penetration Testing Reconnaissance in Physical...
Planning and Scoping
Program Objectives Compare and contrast governance, risk, and compliance...
Platform as a Service
Topics Covered What is Platform as a Service What...
Policies to Mitigate Risk
Topics Covered What is Risk Mitigation? Cybersecurity Risk Mitigation...
Project Basics
Project Objectives Summarize the properties of a project. Classify...
Project Constraints
Project Objectives Given a scenario, predict the impact of...
Project Tools & Documentation
Project Objectives Compare and contrast various project management tools....
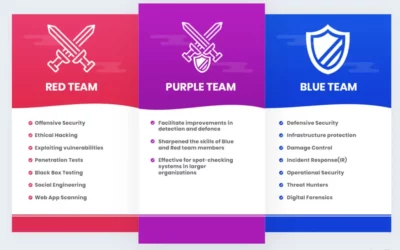
Purple Team (Red Team Interface with Blue Team)
Topics Covered Introduction to Purple Team Why is purple...
Reconnaissance (Information Gathering/Discovery)
Topics Covered What is Reconnaissance? What types of information?...
Recruiting Red Team Members
Topics Covered Skills required Personality Traits Outsourcing vs Developing...